By Stew Webb Federal Whistleblower
President Trump Stop Cyber Terrorism against Stew Webb Whistle blower
The Computer Fraud and Abuse Act (CFAA) [18 U.S.C. Section 1030] makes it illegal for anyone to distribute computer code or place it in the stream of commerce if they intend to cause either damage or economic loss. The CFAA focuses on a code’s damage to computer systems and the attendant economic losses, and it provides criminal penalties for either knowingly or recklessly releasing a computer virus into computers used in interstate commerce.
Someone convicted under the CFAA could face a prison sentence as long as 20 years and a fine of up to $250,000.
I will be posting the entire report proving over 6 million felonies over three years against my email account, my internet service providers and my website stewwebb.com under The Computer Fraud and Abuse Act (CFAA) [18 U.S.C. Section 1030] and Violations of my 1st Amendment Right to freedom of speech and Violations under RICO The Racketeering Influence and Corruption Organization Act plus attempted murders since 2009 because of filings in US District Court in Kansas City for Injunctive Relief from attempted murder using Blackwater Helicopter to lazer and kill this whistle blower then three car crashes from October 2010 – November 2011 which I have not been paid and which the car crashes has disabled this Whistle blower and I am being cheated out of one half of the social security minimum that I am entitled to under US law.
Related
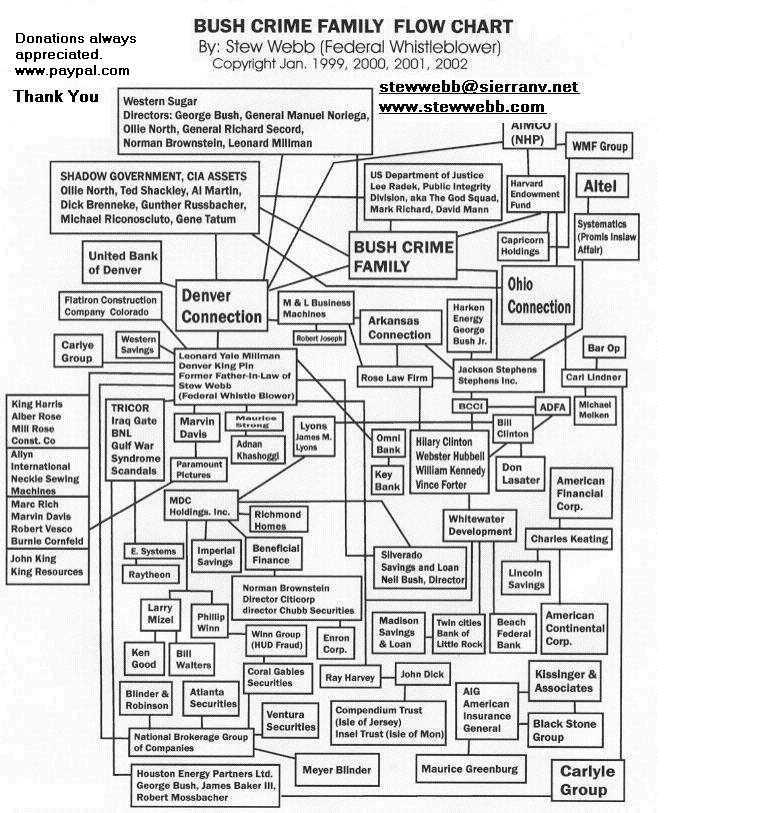
Below are at least 12 or more links to Israel, US DOD, British Intel, Larry Mizel, George HW Bush, Kansas City FBI, Missouri Fusing Center and many others in the US Shadow Government also now being called the Deep State. The Shadow Government is the top of the deep state also known as the Illuminati also known and the Council of 13 also known as the 12 Disciples of Satan, George HW Bush, Larry Mizel, Henry Kissinger, William Grace, Answar Ben Shari, Pope Benidick, David Rockefeller, Patrick WU aka Patrick WY, Meyer Rothchild, Paul Warberg, and I am missing 2 of the 12.
throttling
Tokyo, Japan was blocked by firewall for Directory Traversal in query string: fileName=..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fetc%2Fpasswd at http://www.stewwebb.com/wp-content/plugins/candidate-application-form/downloadpdffile.php?fileName=..%2F.…
2/27/2018 8:30:52 AM (4 hours 53 mins ago)
IP: 54.249.38.229 Hostname: ec2-54-249-38-229.ap-northeast-1.compute.amazonaws.com
Human/Bot: Bot
Browser: Opera version 36.0 running on Win10
Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/49.0.2623.75 Safari/537.36 OPR/36.0.2130.32
NetRange: 54.240.0.0 – 54.255.255.255
[1048576 addresses in this network]
CIDR: 54.240.0.0/12 (54.240.0.0 – 54.255.255.255)
[1048576 addresses in this network]
NetName: AMAZON-2011L
NetHandle: NET-54-240-0-0-1
Parent: NET54 (NET-54-0-0-0-0)
NetType: Direct Allocation
OriginAS: AS16509
Organization: Amazon Technologies Inc. (AT-88-Z)
RegDate: 2011-12-09
Updated: 2012-04-02
Ref: https://whois.arin.net/rest/net/NET-54-240-0-0-1
OrgName: Amazon Technologies Inc.
OrgId: AT-88-Z
Address: 410 Terry Ave N.
City: Seattle
StateProv: WA
PostalCode: 98109
Country: US
RegDate: 2011-12-08
Updated: 2017-01-28
Comment: All abuse reports MUST include:
Comment: * src IP
Comment: * dest IP (your IP)
Comment: * dest port
Comment: * Accurate date/timestamp and timezone of activity
Comment: * Intensity/frequency (short log extracts)
Comment: * Your contact details (phone and email) Without these we will be unable to identify the correct owner of the IP address at that point in time.
Ref: https://whois.arin.net/rest/org/AT-88-Z
OrgAbuseHandle: AEA8-ARIN
OrgAbuseName: Amazon EC2 Abuse
OrgAbusePhone: +1-206-266-4064
OrgAbuseEmail: abuse@amazonaws.com
OrgAbuseRef: https://whois.arin.net/rest/poc/AEA8-ARIN
OrgTechHandle: ANO24-ARIN
OrgTechName: Amazon EC2 Network Operations
OrgTechPhone: +1-206-266-4064
OrgTechEmail: amzn-noc-contact@amazon.com
OrgTechRef: https://whois.arin.net/rest/poc/ANO24-ARIN
OrgNOCHandle: AANO1-ARIN
OrgNOCName: Amazon AWS Network Operations
OrgNOCPhone: +1-206-266-4064
OrgNOCEmail: amzn-noc-contact@amazon.com
OrgNOCRef: https://whois.arin.net/rest/poc/AANO1-ARIN
address 54.249.38.229
Location Tokyo, Tokyo, Japan
IP address 54.249.38.229
Reverse DNS (PTR record) ec2-54-249-38-229.ap-northeast-1.compute.amazonaws.com
DNS server (NS record) x2.amazonaws.com (156.154.65.10)
x3.amazonaws.org (208.78.71.31)
x4.amazonaws.org (204.13.251.31)
x1.amazonaws.com (156.154.64.10)
pdns1.ultradns.net (204.74.108.1)
ASN number 16509
ASN name (ISP) Amazon.com, Inc.
IP-range/subnet 54.249.32.0/19
54.249.32.0 – 54.249.63.255
Domains around 54.249.38.229
IP address #domains
54.249.38.32 1
54.249.38.79 1
54.249.38.85 2
54.249.38.117 1
54.249.38.122 1
54.249.38.125 1
54.249.38.158 1
54.249.38.165 1
54.249.38.187 1
54.249.38.195 1
54.249.38.203 1
54.249.38.214 1
54.249.38.216 4
54.249.38.227 1
54.249.38.236 1
54.249.38.255 14
NetRange: 54.248.0.0 – 54.249.255.255
CIDR: 54.248.0.0/15
NetName: AMAZO-ZNRT1
NetHandle: NET-54-248-0-0-1
Parent: AMAZON-2011L (NET-54-240-0-0-1)
NetType: Reallocated
OriginAS: AS16509
Organization: Amazon.com, Inc. (AMAZO-4)
RegDate: 2012-01-10
Updated: 2012-10-26
OrgName: Amazon.com, Inc.
OrgId: AMAZO-4
Address: Amazon Web Services, Inc.
Address: P.O. Box 81226
City: Seattle
StateProv: WA
PostalCode: 98108-1226
Country: US
RegDate: 2005-09-29
Updated: 2017-01-28
Comment: For details of this service please see
206-266-4064
amazon.com
amazonaws.com
NetRange: 54.240.0.0 – 54.255.255.255
CIDR: 54.240.0.0/12
NetName: AMAZON-2011L
NetHandle: NET-54-240-0-0-1
Parent: NET54 (NET-54-0-0-0-0)
NetType: Direct Allocation
OriginAS: AS16509
Organization: Amazon Technologies Inc. (AT-88-Z)
RegDate: 2011-12-09
Updated: 2012-04-02
OrgName: Amazon Technologies Inc.
OrgId: AT-88-Z
Address: 410 Terry Ave N.
City: Seattle
StateProv: WA
PostalCode: 98109
Country: US
RegDate: 2011-12-08
Updated: 2017-01-28
Your kind Contributions are very much appreciated thank you. – Stew Webb











.jpg)